How to Establish a BYOD Policy
Ever been frustrated by the ancient technology you’re forced to use at the office?
Tech geeks have it especially tough. At home, you’ve always got the latest gadgets. Your smartphone has all the apps you need, you’ve got the latest gizmo in hand shortly after it’s released, and you’ve got your desktop computer hooked up with all of the peripherals exactly the way you want them.
But the office is a different story. You live in fear of carpal tunnel syndrome from contorting your wrists to type on a flat old keyboard, and your monitor resolution is laughable.
And let’s not get started on the software that you’re stuck with. You’re forced to live without all your browser extensions, and forget about your preferred browser (perhaps you’re even still stuck with IE6).
Everything would be so much easier if you could just use all your own devices at work
Turns out, many companies are beginning to agree with you.
On the surface, it seems like a no-brainer. You know you’d be more comfortable and work more efficiently using all the devices and configurations that you’re used to. And your company would sure save a lot of time and hassle if employees were allowed to take care of their own devices.
It seems like a great idea in theory… but in practice, it’s a bit more complicated. Some companies have already discovered the pitfalls of sharing information on outside devices — and that’s why it’s so important for companies to develop an official BYOD (bring your own device) policy.
The potential benefits are great — what company couldn’t use an increase in employee morale and efficiency? But when you’re putting the company’s security at risk, those benefits just aren’t worth it.
Want to convince your company to allow you to bring your own laptop to the office, or maybe you’re considering implementing a BYOD policy at your company? Check out the pros and cons below, and follow the guide to create an official policy that will protect your company from any pitfalls.
Transcript – What’s a BYOD Policy?
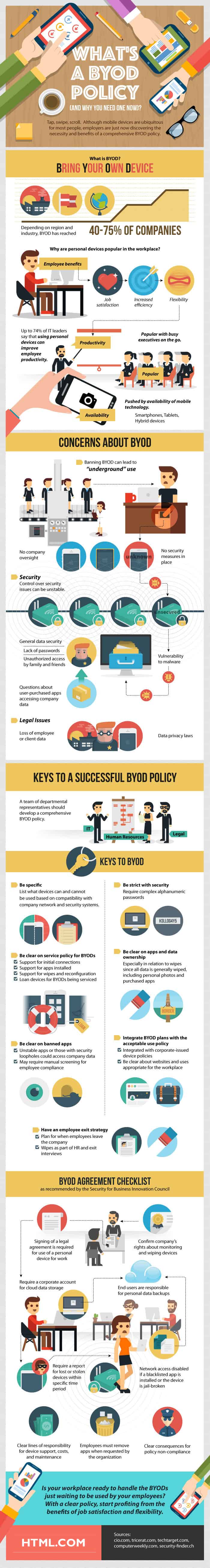
Tap, swipe, scroll. Although mobile devices are ubiquitous for most people, employers are just now discovering the necessity and benefits of a comprehensive BYOD policy.
What is BYOD?
- Bring Your Own Device
- Depending on region and industry, BYOD has reached 40-75% of companies.
- Why are personal devices popular in the workplace?
- Employee benefits
- Job satisfaction
- Increased efficiency
- Flexibility
- Up to 74% of IT leaders say that using personal devices can improve employee productivity.
- Popular with busy executives on the go.
- Pushed by availability of mobile technology
- Smartphones
- Tablets
- Hybrid devices
Concerns About BYOD
- Banning BYOD can lead to “underground” use
- No company oversight
- No security measures in place
- Security
- Control over security issues can be unreliable
- General data security
- Lack of passwords
- Unauthorized access by non-employees
- Questions about user-purchased apps accessing company data
- Less than 1/4 of BYODs that are lost can be remotely wiped of sensitive company data.
- Vulnerability to malware
- Legal Issues
- Data privacy laws
- Loss of employee or client data
Keys to a Successful BYOD Policy
- A team of departmental representatives should develop a comprehensive BYOD policy
- IT
- Human Resources
- Legal
- Keys to BYOD
- Be specific
- List what devices can and cannot be used
- Based on compatibility with company network and security systems
- Be strict with security
- Require complex alphanumeric passwords
- Be clear on service policy for BYODs
- Support for initial connections
- Support for apps installed
- Support for wipes and reconfiguration
- Loan devices for BYODs being serviced
- Be clear on apps and data ownership
- Especially in relation to wipes since all data is generally wiped, including personal photos and purchased apps.
- Be clear on banned apps
- Unstable apps or those with security loopholes could access company data.
- May require manual screening for employee compliance
- Integrate BYOD plans with the acceptable use policy
- Integrated with corporate-issued device policies
- Be clear about websites and uses appropriate for the workplace
- Have an employee exit strategy
- Plan for when employees leave the company
- Wipes as part of HR and exit interviews
- BYOD Agreement Checklist – as recommended by the Security for Business Innovation Council
- Sign a legal agreement for use of a personal device at work
- Require a corporate account for cloud data storage
- Require a report for lost or stolen devices within a specific time period
- Confirm company’s rights regarding in terms of monitoring and wiping devices
- End users are responsible for personal data backups
- Clear lines of responsibility for device support, costs, and maintenance
- Employees must remove apps when requested by the organization
- Network access disabled if a blacklisted app is installed or the device is jail-broken
- Clear consequences for policy non-compliance
Is your workplace ready to handle the BYODs just waiting to be used by your employees? With a clear policy, you can start profiting from the benefits of job satisfaction and flexibility.
Sources
- 7 Tips for Establishing a Successful BYOD Policy – cio.com
- Infographic: What Drives BYOD? – tricerat.com
- BYOD Security Strategies: Balancing BYOD Risks and Rewards – searchsecurity.techtarget.com
- BYOD: Data Protection and Information Security Issues – computerweekly.com
- Why You Need a BYOD Policy Yesterday – tricerat.com
- Realizing the Mobile Enterprise – security-finder.ch
Download this infographic.